Testing Plan for Video Compression, Decompression and Execution
Video
Software testing is the of import to accomplish the quality of the package been developed. It is used to look into application faculty or the package that fulfills the demand of the terminal user. Testing is related to two other procedures like confirmation and proof.
Confirmation: gives verification specifications.
Order custom essay Testing Plan for Video Compression, Decompression and Execution with free plagiarism report
 450+ experts on 30 subjects
450+ experts on 30 subjects
 Starting from 3 hours delivery
Starting from 3 hours delivery
Validation: gives verification necessities.
Trial Plan
The trial program is doing the planning of the overall package. It will run into all the demand for existent clip processing. Quality confidence should be organized to look into each and every functionality. Besides trial program includes following
- Test category to be tested
- Operation property to be tested
- Test event
- Testing environment
- Test out of scope
- Trial agenda
Testing Technique
A Technique has been used are as follows by black-box testing and white box testing. It detects the mistake programmed; keep truth, completeness, and scalability of application developed is called testing.
BLACK BOX Testing
A proving which concentrates merely on the functional demands of an application or package is called a Black-box testing or behavioral testing. Black-box proving efforts to bring out
- Inaccurate or omitted maps
- Interface mistakes
- Mistakes related to information constructions or external information base entree
- Behavior or public presentation mistakes
- Low-level formatting and expiration mistakes.
In this thesis:
Black box proving includes acquiring a petition from a client is proper or non as per the client petition waiter acknowledge. Server indexing client requested information in the database. Indexed information is proper or non, directing of byte by byte information to buffer is maintain the indexing sequence or non. This sort of proving performed in black box testing.
WHITE BOX Testing
White box testing is nil but the complementary to black-box proving. The internal execution of the application can be tested by this testing.
- Buffer storage compress information that acquiring from the database, It is relevant or non. If there are losing index than the information content may be an alteration. So, will prove information compressed in the buffer is right indexed or non.
- The executor extracts the theoretical account, position, and control stage, tested is there are any lost pieces of information or non.
- Controlling information stored in impermanent memory, after completion of sending the requested information to the client commanding information is removed or non.
- Sending clip information compressed utilizing the Huffman algorithm.
- Retrieved information is right or non.
- The client retrieves information after 2 clip decompresses information. After decompressed existent information got by client or non.
Testing Scheme
Testing is an effectual conductivity of antecedently planned activities. A scheme for package proving must supply adjustment for low-level trials that are necessary to verify that a little unit of application has been right implemented every bit good as high-ranking trials that validate major system maps against client demands. Testing schemes can be classified as follows.
Unit of measurement
Unit of measurement proving considers package constituent or faculty as the smallest testable piece of package. It takes the constituent or faculty of the testable package in the application, separates it from the balance of the codification. Then it verifies whether it works as you expect. This type of proving can be done on multiple faculties in analog. It is white box oriented, as it is used to verify the control flow and information flow.
Integration Testing
It is a logical extension of faculty or constituent testing. It chiefly focuses on happening defects which chiefly arise because of uniting assorted constituents for proving. Integration proving purposes at constructing a plan construction by taking integrity tested faculties. It conducts trial to uncover mistakes associated with interfacing. Once we have finished with unit proving, the following undertaking is to execute incorporate proving. Unit tested faculties are taken and assemble together and execute incorporate proving. In this proving, one or more faculties are tested at a clip w.r.t their functionality.
SYSTEM Testing
It verifies the full merchandise, after uniting all package and hardware constituents and validates it harmonizing to original undertaking demands. The chief purpose of the system proving is to accomplish a successful execution of the computing machine based system utilizing a sequence of trials. In the peculiar, each trial may hold different intents but the purpose behind all is to verify the combination and working of system elements.
Trial Case
Some conditions or variables followed by the examiner to measure the effectivity of any application or system called as Test instances. It may be an individual measure, or multiple stairs, to guarantee the rightness of an application. A predictable consequence or result is can be shown as follows. Table 9.4 shows the trial instance for the proposed system, as table follows by the trial instance name, the measure requires to acquire expected consequence, an expected consequence from the proposed system, an existent how system response, and in conclusion comment for trial instance to be base on balls or fail.
| Test Case No. | Test Case Name | Stairs | Expected Consequence | Actual Consequence | Remark |
| Case 1 | Client Request | Store information in server-client can bespeak merely for this information. | Request accept by the waiter and acknowledge | Request accepted by the waiter and acknowledge to the client. | Base on balls. |
| Case 2 | Server information indexing | Server shop information in the database as per client petition database indexing that information. | Indexing as per the existent sequence of a picture file | Indexed picture file to direct information to buffer as per the existent sequence of a picture file. | Base on balls |
| Case 3 | Buffer acquire information from the database as per indexed | The database sends information to the buffer in bytes | Data infusion in byte format for buffer procedure | Data extracted in byte format and send to buffer | Base on balls |
| Case 4 | Compress information in the buffer | Buffer compacting information that got from the database | Compress Data as per acquiring byte from database | Data that got from the database in bytes | Base on balls |
| Case 5 | Extracting theoretical account, position, and command portion from tight picture file in bytes | Executor extract theoretical account, position, and account information and those information shop in an array of bytes | Extraction of 3 parts and measure theoretical account | Extract merely view portion there is no any back land sound consequence | Fail |
Table – 9.4: Trial instances
RESULT Analysis
For ciphering the public presentation of the proposed system and besides doing comparative analysis with the consequence been generated from the experimental rating.
- Compaction Comparison:
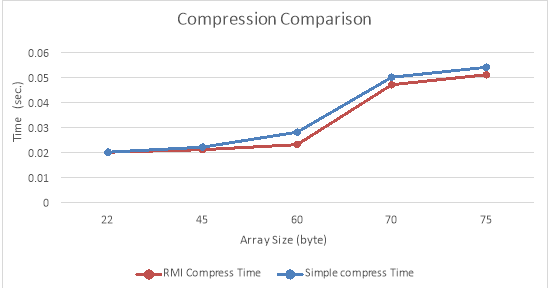
Figure – 10.1 ( a ) : Compaction Comparison
| RMI Compress Time | Simple compress Time | Array size |
| 0.08 | 0.082 | 22 |
| 0.082 | 0.089 | 45 |
| 0.094 | 0.1 | 60 |
| 0.1 | 0.11 | 70 |
| 0.110 | 0.12 | 75 |
Decompression Comparison:
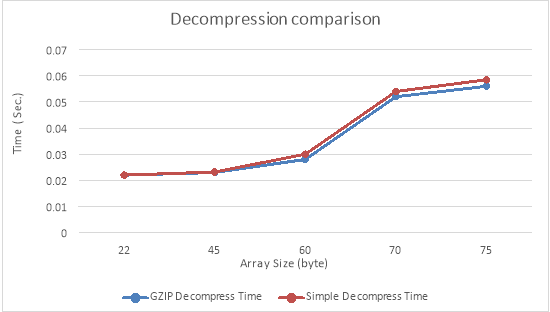
Figure – 10.1 ( B ) Decompression Comparison
| GZIP Decompress Time | Simple Decompress Time | Array Size |
| 0.022 | 0.022 | 22 |
| 0.023 | 0.0232 | 45 |
| 0.028 | 0.03 | 60 |
| 0.052 | 0.054 | 70 |
| 0.056 | 0.0585 | 75 |
Transmission of information utilizing J2ME RMI ( Between 2 machines )
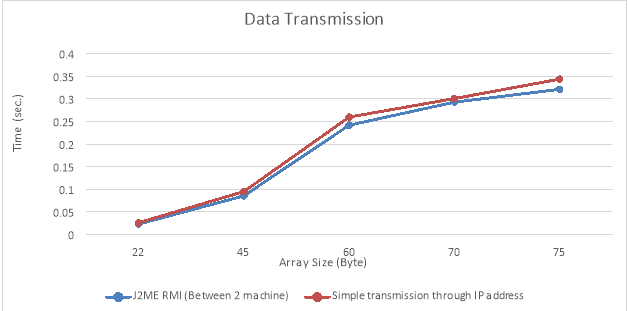
Figure – 10.1 ( degree Celsius ): Transmission of Data utilizing J2ME RMI
| J2ME RMI ( Between 2 machine ) | Simple transmission through IP reference | Array Size |
| 0.63 | 0.66 | 22 |
| 0.656 | 0.695 | 45 |
| 0.742 | 0.776 | 60 |
| 0.793 | 0.811 | 70 |
| 0.8214 | 0.841 | 75 |
Transmission of information utilizing J2ME RMI ( Using 1 machine) :
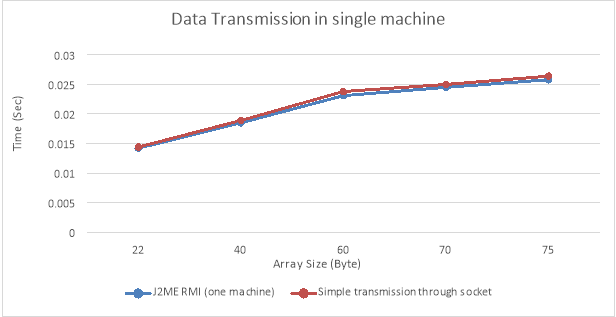
Figure – 10.1 ( vitamin D ): Data transmittal in individual machine
| J2ME RMI ( one machine ) | Simple transmittal through socket | Array Size |
| 0.642 | 0.644 | 22 |
| 0.785 | 0.789 | 40 |
| 0.831 | 0.862 | 60 |
| 0.885 | 0.89 | 70 |
| 0.918 | 0.934 | 75 |
Comparison of Proposed System with the Current System.
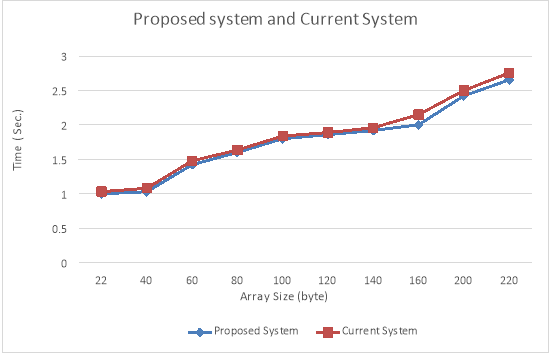
Figure – 10.1 ( vitamin E ): Proposed system and Youtube comparing
| Proposed System Time Taking | YouTube Time Taking | Array Size |
| 1.2021 | 1.032 | 22 |
| 1.031 | 1.082 | 40 |
| 1.423 | 1.48 | 60 |
| 1.602 | 1.637 | 80 |
| 1.8 | 1.84 | 100 |
| 1.86 | 1.89 | 120 |
| 1.92 | 1.96 | 140 |
| 2.003 | 2.15 | 160 |
| 2.423 | 2.501 | 200 |
| 2.654 | 2.756 | 220 |
Main
Figure-11.1: Main GUI
Video

Figure- 11.2: Video choice
VIDEO PLAYER ( Small size picture ):

Figure – 11.3 ( a ): Small size picture participant

Figure – 11.3 ( B ): HD picture participant
AUDIO Choice
Figure – 11.4 ( a ) : Audio choice

Figure – 11.4 ( B ) : Audio Player
- Decision:
This research proposed offloading picture compaction, decompression, and executing of the picture at the server-side. Compaction utilizing the Gzip method is more effective than any other compression technique. Gzip usage Quadtree method every bit good as the Huffman algorithm to compact the information utilizing this sort of compaction of information we can state that information is more confidential while directing from waiter to client. Proposed system usage buffer storage. It will bring information from the database in bytes, compress information, and send it to the executor for the farther procedure. Buffer storage usage Data buffer algorithm to hive away information and direct information as per demand to the executor. The executor extract the theoretical account, position, and command portion from the picture file and direct the theoretical account and position portion to the requested client and shop control portion as impermanent information. This proposed system is more confidential than any other unrecorded cyclosis of a picture or any other picture downloader. The proposed system is taking fewer clips than any other system for unrecorded cyclosis or download. When we are directing theoretical account, position, and command portion together to any client at that clip command portion taking more clip to put to death. But, with this proposed system we are covering merely with theoretical account and position portion. System Extract command portion and usage Huffman algorithm at directing clip, it will take less clip than control information sent over the web.
Reference
- Adaptive Offloading for Pervasive Computing, Published by the IEEE CS and IEEE ComSoc,1536-1268/04/ $ 20.00 © 2004 IEEE
- Fuzzy logic in the control system: Fuzzy logic accountant – Part I, CHUEN CHIEN, pupil member, IEEE, IEEE dealing on the system, MAN and cybernetics, vol.20, NO-2, March / April. 1990
- Transparent and Dynamic Code Offloading for Java Applications, Nicolas Geoffray, Gael Thomas, and BertilFolliotLaboratoired, Informatique de Paris 6 8 herbs of grace du Capitaine Scott, 75015 Paris France
- Image Encoding Using Block-Based Transformation Algorithm, Mohammad Ali, BaniYounes and AmanJantan, IAENG International Journal of Computer Science, 35:1, IJCS_35_1_03.
- EMBEDDING OF EXECUTABLE FILE IN ENCRYPTED IMAGE USING LSB MECHANISM, P.Sathish Kumar, Mr. C.BalaKrishnan, International Conference on Information Systems and Computing ( ICISC-2013 ), INDIA, ISSN 2250-2459 ( Online ), An ISO 9001:2008 Certified Journal, Volume 3, Particular Issue 1, January 2013
- A GENERIC PERFORMANCE EVALUATION MODEL FOR THE FILE SYSTEMS, Farid, SD Joshi, Manjusha Joshi; International diary of Computer Engineering & A; Technology ( IJCET ),5,1
- Profiling Skype Video Calls: Rate Control and Video Quality, Xinggong Zhang, Yang Xu, HaoHuy, Yong Liu, Zongming Guo, and Yao Wang.
- Video Compression Techniques – A Comprehensive Survey, M.Atheeshwari, K.Mahesh, International Journal of Advanced Research in Computer Science and Software Engineering, Volume 4, Issue 1, January 2014 ISSN: 2277 128X.
- Video Compression Techniques – A Comprehensive Survey, M.Atheeshwari, K.Mahesh, International Journal of Advanced Research in Computer Science and Software Engineering, Volume 4, Issue 1, January 2014 ISSN: 2277 128X.
- Fox et al. , “Adapting to Network and Client Variation Using Active Proxies: Lessons and Positions, ” IEEE Personal Comm. , Aug. 1998, pp. 10–19.
Cite this Page
Testing Plan for Video Compression, Decompression and Execution. (2018, Aug 10). Retrieved from https://phdessay.com/testing-plan-for-video-compression-decompression-and-execution/
Run a free check or have your essay done for you


