Embedding and Extracting of Secret Data
BLOCK DIAGRAM
TRANSMITTER Section
In Transmitter subdivision there are 3 parts:
Order custom essay Embedding and Extracting of Secret Data with free plagiarism report
 450+ experts on 30 subjects
450+ experts on 30 subjects
 Starting from 3 hours delivery
Starting from 3 hours delivery
Figure 1 The block diagram Transmitter subdivision
In Transmitter subdivision there are 3 parts:
- Input screen Images
- Encoder subdivision
- Output Stego Image
The screen image used for the proposed strategy to be taken as an input Original screen Image which is used for implanting secret informations in it.
Encoder unit is composed of Generation map and secret keys. Encoder determines whether it is smooth country or edged country depending upon the threshold value. In smooth country little figure of spots implanting compared to inch country.
Finally at the sender subdivision Stego image is generated which is a combination of secret keys and screen images.
RECEIVER Section
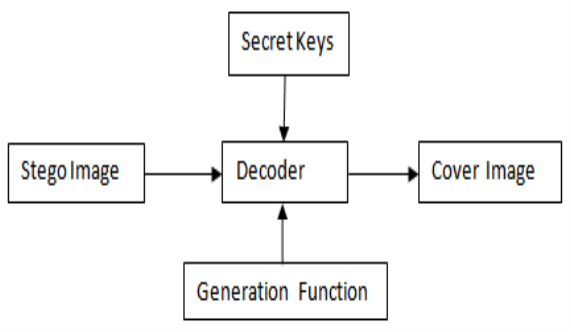
Figure 2 The block diagram Receiver subdivision
In Receiver subdivision there are 3 parts:
- Input Stego Images
- Decoder subdivision
- Output Cover Image
The Stego Image is taken as an input to the receiver side. The Stego image is decoded right by utilizing secret keys and coevals map to obtain the screen image.
The secret keys used in both the sender and receiver side are same. Pixels in the border countries are embedded by Q-bit of secret informations with a larger value of Q than that of pels placed in smooth countries.
Chapter 4
PROJECT METHODOLOGY
The proposed adaptative strategy
There are five secret keys viz. R1, R2, v1, v2, T and 1 6 v1, 1 6 v2, ( v1 + v2 ) & lt ; 6. The mean different values of a four-pixel block are utilized to sort the block as a smooth country or an edge country. The scope of mean different value is partitioned into two different degrees, smooth degree and border degree. Q-bit of the secret information is embedded in Pixels located in the block, where Q is decided by the degree in which the norm different values belong to. In the implanting procedure of secret informations, harmonizing to the secret keys v1 and v2, the smooth degree will utilize lower value v1 while the border degree uses greater value v1 + v2. The information embedding procedure is given in Section 2.1.1 and the extracting stage is described in Section 2.1.2.
The implanting stage in proposed adaptative method
The original image is separated into non- overlapping four-pixel blocks. For each block, there are four neighboring pels ‘Pi, j’ ; ‘Pi, j+1’ ; ‘Pi+1, j’ ; ’ Pi+1, j+1’ and their corresponding grey values are y0, y1, y2, y3, severally.
The undermentioned flow chart shows elaborate working of implanting stage in proposed adaptative strategy











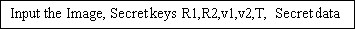








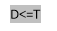
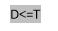





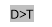




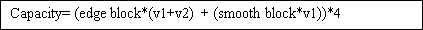


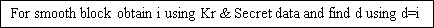

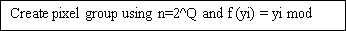











The elaborate embedding stairss are as follows.
Measure 1:
Generate Two sets Kr and Kc utilizing threshold Hr ( R1, v1 ) and Hc ( R2, v2 ) , severally. Via sets Kr and Kc form a discrepancy of a Cartesian merchandise viz. , Kr _ Kc. Set Kr _ Kc generates an ordered set of combinations of Kr and Kc with 2v1 • 2v2 = 2v1+v2 elements ( Eq. ( 1 ) ) .
Kr*Kc = { Kria”‚a”‚Kcja”‚ , Kri ˆ Kr, Kcj ˆ Kc, i=1,2,3... .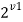 }
}
=1, 2, 3... ..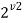 .… ( 1 )
.… ( 1 )
Measure 2:
Calculate the mean difference value D, Which is determined by
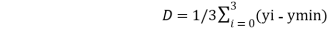 … . ( 2 )
… . ( 2 )
Where ymin is ymin=min { y0, y1, y2, y3 }
Measure 3:
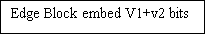
Using Threshold T and D find smooth block, Edge block and mistake block.
i.e.
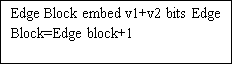
a ) If D & lt ; =T, D belongs to Smooth block.
B ) If D & gt ; T, D belongs to Edge block.
degree Celsius ) If D & lt ; =T and ( ymax- ymin ) & gt ; 2*T+2, D belongs to Error block.
Measure 4:
Repeat measure 3 for full image
Measure 5:
Capacity= ( ( border block* ( v1+v2 ) ) + smooth block*v1 ) ) *4
Measure 6:
For smooth block obtain I utilizing Kr & A ; Secret informations and find‘d’ .
For border block: -
d=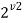 ? ( i-1 ) +j... . ( 3 )
? ( i-1 ) +j... . ( 3 )
For smooth block: -
d= I... .. ( 4 )
Measure 7:
Create pel group utilizing 'n=2^Q’ .
degree Fahrenheit ( Lolo ) =yi mod n+1 … . ( 5 )
Measure 8:
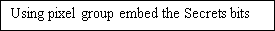
Using pel group embed the Secrets spots
Measure 9:
If No Of Secret Data=Capacity, travel to step 10 else measure 6.
Measure 10:
Apply mistake cut downing process for minimising perceptual deformation between screen & A ; stego image.
Example: -
Assume we have a block part with 4 neighboring pel values ( 210, 237, 198, and 183 ) , and the secret information informations for implanting in original image are ‘10010101110000111010’ .
Suppose v1 = 2, v2 = 3, R1 = 257, R2 = 36 and T = 25. Here first coevals map Kr= { 000,100,010,011,001,110,101,111 } is created by utilizing Hr ( R1, V1 ) i.e. Hr ( 257,2 ) and 2nd coevals map Kc = { 01,11,10,00 } is generated by utilizing Hc ( R2, V2 ) i.e. Hc ( 36,3 ) , after that by utilizing equation ( 2 ) calculate the mean different value ‘D’ = ( 96/3 ) =32 which is greater than threshold value T, so the present block has been positioned in border country and is embedded Q = 5 Numberss of spots of secret informations in each peculiar pel. Hence, sum entire 4 * 5 = 20 spots are embedded in given block.
Here for first pel into the block, e.g. y0 = 210, the initial part of secret informations ’10010’ is split into the two sub-strings ‘100’ and ‘10’ . Then, we get one = 2 and j = 3 because the 6th constituent of Kr is ‘100’ and 4th constituent of Kc is ‘10’ .
Harmonizing to equation ( 3 ) , we compute‘d’ utilizing 8 * ( 2–1 ) +3 = 11.
After that, the pel group ‘G’ is formed for the pel value y0 = 210 with n =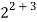 = 32. Here g 19= 210. Finally, the stego-pixel y`0 can be achieve from the dth component of G, i.e. y`0 = g24 = 202. Likewise we can happen leftover stego-pixel y`1 = 249, y`2 = 201, y`3 = 185 and therefore stego-block ( 202,249,201,185 ) is achieved. After using readjusts process we get concluding stego-block ( 202, 241, 201, and 185 ) .
= 32. Here g 19= 210. Finally, the stego-pixel y`0 can be achieve from the dth component of G, i.e. y`0 = g24 = 202. Likewise we can happen leftover stego-pixel y`1 = 249, y`2 = 201, y`3 = 185 and therefore stego-block ( 202,249,201,185 ) is achieved. After using readjusts process we get concluding stego-block ( 202, 241, 201, and 185 ) .
The pull outing stage in proposed adaptative strategy
Like the implanting procedure, Partition the stego-image into four-pixel blocks.
The undermentioned flow chart for pull outing informations from stego image in proposed adaptative strategy explains elaborate working flow



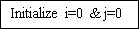

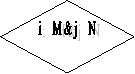





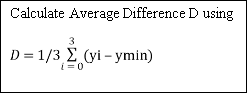




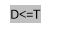
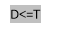





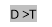








The undermentioned stairss are executed to pull out the secret information.
Measure 1: Input signal Stego Image, Secret keys R1, R2, v1, v2, T
Step2: Generate Kr & A ; Kc Using R1, R2, v1, v2
Step3: Initialize i=0 & A ; j=0
Measure 4: if I & lt ; =M & A ; j & lt ; =N, travel to step 5 else halt.
Measure 5: Calculate Average Diff ‘D’ utilizing combining weight. ( 2 )
Measure 6: Exploitation Threshold ‘T’ and ‘D’ find smooth
block, Edge block and mistake block.
i.e.
a ) If D & lt ; =T, D belongs to Smooth block.
B ) If D & gt ; T, D belongs to Edge block.
degree Celsius ) If D & lt ; =T and ( ymax-ymin ) & gt ; 2*T+2, D
belongs to Error block.
Measure 7: Create pel group utilizing n=2^Q and
degree Fahrenheit ( Lolo ) =yi mod n+1
Measure 8: Determine place information‘d’ .
Measure 9: From‘d’ extract secret informations.
Example
For case, we extract the implanting illustration ( 151, 88, 193, and 133 ) , which is shown in the before subdivision. Assume v1 = 2, v2 = 3, R1 = 257, R2 = 36 and T = 25. The coevals map Kr = { 001, 110,101,010,111,100,011,000 } is formed by utilizing Hr ( R1, V1 ) i.e. Hr ( 257,2 ) and Kc = { 00,10,11,01 } by utilizing Hc ( R2, V2 ) i.e. ( 36,3 ) are produced.
Here D & gt ; T, hence this block is placed in edge country and hence Q = v1 + v2 = 3 + 2 = 5 spots have embedded into each Pixel in the block. In present block sum, 4 • 5 = 20 spots are embedded. Let us see 3rd pel into the block ( e.g. y `` 2 = 202 ) . The pel group G is created for value 202 via Eq. ( 5 ) With n = 32.
We create the variant Cartesian merchandise Kr _ Kc, which is value 202 with n = 22+3= 32. The place of stego-pixel 202 in G is 1, because vitamin D = ( 202 mod 32 ) + 1 = 3. The piece of binary secret informations ‘00001’ can be extracted because ‘00001’ is the 3rd constituent of Kr _ Kc.
In the same manner, has extracted the secret information subdivision ‘10010’ for Y``0, ‘10111’ for Y``1and ‘11010’ for Y``3. Finally we achieve ‘10010101110000111010’ which is the similar secret information informations in the implanting illustration of before subdivision.
Cite this Page
Embedding and Extracting of Secret Data. (2018, Aug 22). Retrieved from https://phdessay.com/essay-about-embedding-and-extracting-of-secret-data/
Run a free check or have your essay done for you


