Mine Sweeping System Using Image Processing
MINE SWEEPING SYSTEM USING IMAGE Processing
Abstractions:
Mine sweeping system is entirely designed for observing mines in peculiar user defined country. It uses a Java application from the user country and besides it consists of automaton which plays a cardinal function in the full system. The Java application and the automaton system works together to give an efficient system. The Java application is besides known as waiter and the automaton system communicate each other through wireless transmittal. In this system the human contact with the automaton is non required. The Java application is used to command the full mine sensing procedure. The optical flow vector, the automaton alliance and practical map of the location of the automatons are displayed on the screen of the waiter computing machine. Besides, the antecedently consequences that is the automatons that has searched for mines will besides be available or displayed for the user. So, that no demand of hunt for mines once more and once more in same country or practical grid. The obtained database consequences are so uses to optimise thee mine brushing procedures in the hereafter through a LRU ( Least late used ) algorithm.
Order custom essay Mine Sweeping System Using Image Processing with free plagiarism report
 450+ experts on 30 subjects
450+ experts on 30 subjects
 Starting from 3 hours delivery
Starting from 3 hours delivery
The Robot system is aligned with a camera and uses a self-navigating algorithm with the obstruction turning away implemented utilizing optical flow. The optical flow which is produced within the milieus of the automaton system is registered utilizing the on board camera and by utilizing image processing methods like Image cleavage, Edge sensing and grouping, average filtrating thresholding procedure and by the vector computations, the hacking can be obtained. The automatons will work in a spontaneous practical grid and a existent clip map of the mine sweeping operation is displayed on the waiter system. Actually, the automatons will cipher the really shortest way within the grid while seeking and observing for the mines. The automatons commune with each other utilizing swarm engineering in order to carry through the undertaking.
Introduction:
The robotic usage of this mine sensing is a new procedure whereas the procedure of mine sensing is chiefly carried over by the worlds itself. They used to have on some protective cogwheel and some instruments with which they detect mines. There is a batch of hazard involved in this manner of mine sensing as no 1 can think the happening or the appendage of the blast. Hence so the usage of manual automatons in which they are guided by a user to observe or study a peculiar 1 for a mines therefore came into being. But these manner of observing mines was non much helpful as the manual navigate of the automaton of a certain country becomes tiresome largely over a big terrain.
Therefore the demand for automatic automaton comes over when the user is non all required in voyaging the automaton. The robot hunt in a given country for the mines and the co-ordinates of their places are often sent to the waiter system. These automatons are plotted of a practical grid which is produced on the waiter system and their location can be tracked down. When a mine is detected the co-ordinate is sent back to the sever system and the symbol is marked on the practical grid denominating the sensing of mine such as co-ordinates, topographic point, clip, country all stored in the database. The user can so analyze the database to acquire the necessary information narrow down the hunt country. We used methods such as shortest way algorithm and chiefly image processing for obstruction turning away. Engagement of homo in the full sensing is non at all needed or zero.
CONCEPTS AND FEATURES
Optical flow
Optical flow or ocular flow is the form of evident gesture of objects, surfaces and borders in a ocular scene caused by the comparative gesture between an perceiver and the scene [ 1 ]
Optical flow computation utilizing Lucas cascade method
The gesture of borders, surfaces and objects in a scene which raised by the gesture between an perceiver and scene is known as optical flow. The optical flow can be applied is obstacle turning away and self-alignment of driving circuit of the automaton.
Calculation of optical flow
Let us see two frames of clip T and a?†t at a place. The optical flow is calculated between this frames with the aid of a Taylor series method by utilizing partial derivation based on spacial and temporal coordnates. For a 2D+Tdimensional instance ( 3D orN-D instances are similar ) a voxel at location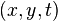 with strength
with strength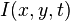 will hold moved by
will hold moved by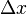 ,
,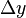 and
and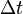 between the two image frames, and the followersbrightness stability restraintcan be given:
between the two image frames, and the followersbrightness stability restraintcan be given:
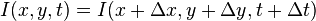
Assuming the motion to be little, the image restraint at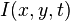 withTaylor seriescan be developed to acquire:
withTaylor seriescan be developed to acquire:
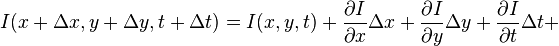 H.O.T.
H.O.T.
From these equations it follows that:
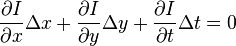
or
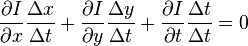
which consequences in
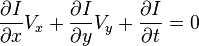
where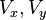 are the
are the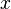 and
and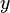 constituents of the speed or optical flow of
constituents of the speed or optical flow of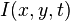 and
and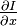 ,
,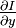 and
and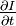 are the derived functions of the image at
are the derived functions of the image at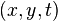 in the corresponding waies.
in the corresponding waies.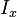 ,
,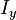 and
and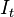 can be written for the derived functions in the followers.
can be written for the derived functions in the followers.
Therefore:
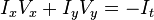
or
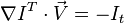 [ 1 ] & A ; [ 2 ]
[ 1 ] & A ; [ 2 ]
This is an equation in two terra incognitas and can non be solved as such. This is known as theaperture problemof the optical flow algorithms. To happen the optical flow another set of equations is needed, given by some extra restraint. All optical flow methods introduce extra conditions for gauging the existent flow.
In the mine sensing procedure optical flow is used for chiefly observing the object, hacking and besides for the robot pilotage.
IMAGE SEGMENTATION
Image cleavage is the procedure of partitioning a digital image into multiple sections which are sets of pels, besides known as ace pels. The end of cleavage is the simplify and/or alteration the representation of an image into something that is more pregnant full and easier to analyse. Image cleavage is typically used to turn up objects and boundaries which include lines, curves. In image more exactly image cleavage is the procedure of delegating a label to every pel in an image such that pels with the same label portion certain features.
The basic measure for image retrieval by mercantile establishment is the computation of the ocular characteristics.
The necessity to observe the object as a whole and non merely portion of it has been approved utilizing a intercrossed cleavage technique based on border sensing, part growth and optical flow processs.
Image cleavage proves to be an of import measure in ciphering the navigational consequences of the automaton system. [ 1 ] & A ; [ 2 ] .
Detection is based on object colour or strength contrast with the environing background. Regardless of the type of detector noise is ever present for cut downing these types of noises we use assorted types of filters.
Median Filter
Medium filter is a nonlinear method used to have noise from images. It is widely used as it is really effectual at taking noise while continuing borders. The average filter plants by traveling through the image pel by pel, replacing each value with the average value of vicinity pels. The form of neighbours is called the window, which pixel by pel over the full image. The median is calculated first screening all the pel values from the window into numerical over, and so replacing the pel being considered with the in-between pel value [ 3 ]
Threshold Method
It is besides known as image threshold. In this method, we introduce a new mechanism for observing the landmine. We merely convert the grayscale and cold images into binary or block/white images with specific threshold value or may be varies.
Atmega 32 microcontroller
The microcontroller we use in the mine sensing procedure for cryptography is the Atmega 32 which has characteristics such as.
- High public presentation, low power Atmel 8-bit micro accountant
- Advanced RISC architecture
- 133 powerful instructions- most signal clock rhythm executing
- 32x8 general intent working registry + peripheral control registry
- Fully inactive operation [ ]
The microcontroller along with the L298 will be used to run the automaton automatically.
Figure: Atmega 32 Microcontroller constellation
Xbee pro communicating faculty
The interaction between the automaton system and waiter system is formed through a Xbee faculty which acts as a trans receiver by procuring consecutive communicating utilizing the UART [ ] .
Consecutive Communicationss
The Xbee/Xbee-pro RF faculties interface to a host device through a logic – degree asynchronous consecutive port. Through its consecutive port the faculty can interact with any logic and electromotive force compatible VART ; or through a degree transcriber to any consecutive device.
UART informations flow
Devicess that have a vart interface can link straight to the pins of the RF faculty.
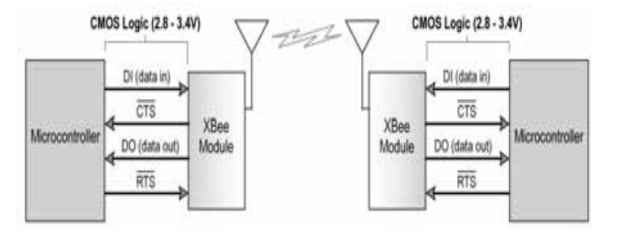 Figure: UART environment Xbee pro system
Figure: UART environment Xbee pro system
Flow Control DI ( Data In ) Buffer
When the consecutive information enters RF faculty through the DI pin, the information is stood in the DI buffer until it can be processed.
Hardware flow control ( CTS ) when the DI buffer is 17bytes off from being full ; by default, the faculty assert CTS to signal to the host device to halt directing informations CTS is re – asserted after the DI buffer has 34 bytes of memory available.
Flow control DO ( Data Out )
When the RF information is received, the informations so enters the DO buffer and is sent out the consecutive point to a host device. Once the DO buffer reduces capacity, any extra entrance RF information is lost.
Hardware flow control ( RTS ) : If RTs is enabled for flow control, informations will non be sent out the DO buffer every bit long as RTS is de- asserted.
Therefore in this manner Xbee pro faculty questions to be an efficient trans receiver which initiates a 2nd VART channel. We create a templet foremost to carry through the papers processing demands. The others services will merely necessitate individual clip activation.
SYSTEM DESIGN:
The full mine sweeping system is categorized into three parts. They are:
- Waiter with Java Application
- Robot system with drove engineering
- Wireless communicating system
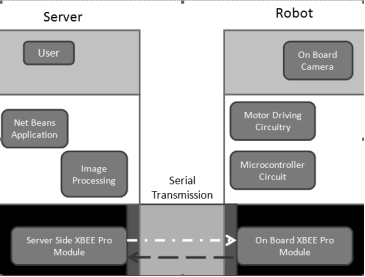
Figure: Block diagram system of Mine brushing
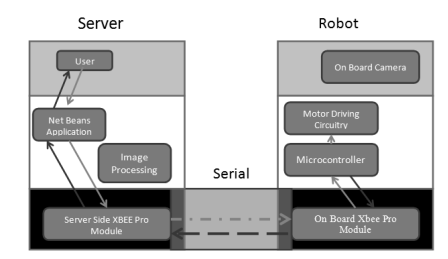
Figure: Microcontroller and architecture communicating
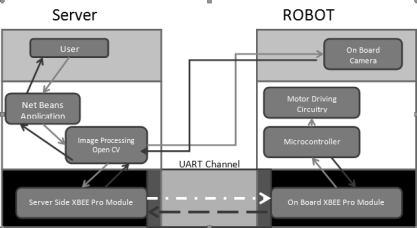
Figure: On Board camera and system communicating
- With the aid of net beans application the user controls the full system. At first the user writes a “start” bid in the Java application. Data will be send to the UART channel through wireless consecutive communicating.
- The start bid is received by the GB Xbee faculty on the automaton system and it triggers the micro accountant.
- After triping the micro accountant it invariably transmit a signal to the driving circuit with the aid of UART channel which portray the practical grid.
- The alterations are deciphered by the Java application and it was created on GEY at the same clip.
- This methodological analysis proceeds the circuit until the automaton achieves at the terminal of the self-created practical map.
- When the micro accountant is triggered it sends informations non merely to the drive circuit but besides to on board IP camera through a radio web device ( router ) to get down the image processing faculty.
- After triping of the IP camera it captures the images of the practical grid and so it sends the information to the image processing faculty in which image cleavage optical flow consequences are generated.
- After finishing of the cringle the automaton sends a “stop” bid to the waiter.
Software demands specification
To put to death the mine sweeping system the user foremost enter the application
- The automaton starts its procedure of seeking when it receives bid from the waiter
- The automaton more over follows a optical flow which can be obtained by utilizing the on board IP camera. With the aid of optical flow method the automaton can avoid the obstructions and it itself align a practical map.
- The automaton so selects a shortest way on the practical grid to observe the mines.
- In this procedure the camera gaining control the image and the informations will be send to the image processing faculty in which mines can be detected by image cleavage procedure.
- After the image cleavage the information will be send to the waiter and shop in a information base.
- Here LRU algorithm is used to better the mine searching, observing and efficiency.
Premises
The distance between the client and the automaton should non be exceeded more than 500mtrs for good consequences.
Dependences
The connexion strength of UART is changeless. The automaton system must hold a changeless power supply all the times for accurate consequences.
System characteristics
The system consists of different characteristics to individual the operations. They are chiefly divided into: -
Database Storage
In this system this database storage plays a chief function. This storage system is used to hive away the images which was taken by on board camera. Here SQL database is developed and used to hive away consequences the automaton system and with the aid of JDBC connexion it was connected to java application
Precedences
With the aid of database the information will be stored manipulate and updated all the informations performed by the automaton is on the constituents. The illustrations are mine figure, location or country, count of mines etc.
FunctionalRequirements
The functional demands are nil but characteristics which are provided to stop users the full system has 3 bomber faculties they are
- Java application faculty
- Image processing faculty
- Robot faculty
Java application faculty
Java faculty is chief portion in the system from this lone the user starts the procedure by come ining the country of practical grid with this application we can besides see the full map with the aid of UART in which automaton performs operations. After finishing operations the applications shows the consequence for users java beans 7.0 is used to develop this application.
Image processing faculty
This faculty plays an of import key in the full system. By this the designation and localisation of mines was done. Here by utilizing image cleavage the mark is identified by the size form and visual aspect, this procedure is done by labelling procedure. In the image cleavage at first the gaining control image is labeled in to parts and so it converted in to black and white image so it subdivide the image harmonizing at that place sizes, forms and constructions. By utilizing these features the mark can be estimated of a mark assurance degree. Image cleavage is non sufficient for placing the mines so we use different mine field forms which can be find in survived part.
Robot system faculty
Thisconsists of micro accountant which generates the map and performs the operation when user gives a bid.
Safety and Security Requirements
- Due to connexion failures and micro accountant lapses the system may be crashed to over this state of affairs the robot resets and show approximately message to the user.
- The radio web is based on SSID user and watchword, which consists of unafraid connexion.
Applications
- It consist of user friendly GUI.
- Known human contact is needed.
- All the communicating is through radio and web.
- The user can manually overrule the system.
Conclusion
The chief of the research is to develop a system which has a capableness of finding an object or mine. Here we used feeling techniques image cleavage and acknowledgment and faculties
Cite this Page
Mine Sweeping System Using Image Processing. (2018, Aug 02). Retrieved from https://phdessay.com/mine-sweeping-system-using-image-processing/
Run a free check or have your essay done for you


