Cloud security architecture based on fully homomorphic encryption
Abstraction
Cloud Computing is a new environment in computing machine oriented services. The high costs of web platforms, development in client demands, informations volumes and weights on response clip pushed companies to migrate to Cloud Computing supplying on demand web facilitated IT Services.
Cloud storage empowers users to remotely hive away their information and delectation in the on-demand high quality cloud applications without the affliction of local hardware direction and programming disposal. In order to work out the job of informations security in cloud computer science system, by presenting to the full homomorphism encoding algorithm in the cloud calculating informations security, another kind of information security solution to the insecurity of the cloud computer science is proposed and the scenarios of this application is hereinafter constructed, This new security agreement is wholly fit for the processing and retrieval of the encrypted informations, successfully motivating the broad relevant chance, the security of informations transmittal and the stockpiling of the cloud computer science.
Order custom essay Cloud security architecture based on fully homomorphic encryption with free plagiarism report
 450+ experts on 30 subjects
450+ experts on 30 subjects
 Starting from 3 hours delivery
Starting from 3 hours delivery
Keyword: Cloud storage, Data security, to the full homomorphic encoding
Introduction
Enterprises are the speedy nearing new advanced clip in which we store our information and execute our excessive calculation remotely. With the usage of cloud there are legion points of involvement in disbursals and usefulness, but the issue with the cloud is secret informations may non be secure. Today, endeavors are looking towards cloud calculating environment to spread out their on-premise substructure, but most can non afford the cost of the danger of trading off the security of their applications and information. Recent progresss in Fully homomorphic encoding ( FHE ) allows us to execute arbitrarily-complex dynamically picked calculations on encrypted informations, despite non holding the secret decoding key. Processing encrypted informations homomorphically requires greater figure of calculations than treating the information unencrypted.
Scientifically talked is a homomorphic cryptosystem, a cryptosystem whose encoding map is a homomorphy and therefore conserves group operation performed on cypher texts. The two group operations are the arithmetic add-on and generation. A homomorphic encoding strategy is said to be linear if the followerss holds –
E ( x+y ) = E ( x )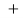 E ( Y )
E ( Y )
What 's more it is said to be multiplicative if –
E ( x, Y ) = E ( x ) * E ( Y )
Where E characterizes an encoding map.
The cryptosystem that support either of the two operations are said to be partly homomorphic encoding system, and the one time that supports both the add-ons and generations of cypher texts is called as to the full homomorphic encoding ( FHE ) .
Cloud computer science and fully homomorphic encoding
The patterned advance of FHE has empowered the cloud service suppliers a better attack to guarantee confidentiality and privateness of user informations. a solution to the old unfastened issue of developing a to the full homomorphic encoding strategy. This thought, once called a privateness homomorphy, was presented by Rivest, Adelman and Dertouzous [ 3 ] shortly after the innovation of RSA by Rivest, Shamir and Adleman.
To supply the better security we are traveling to widen the security solution for cloud calculating with the aid of to the full homomorphic encoding cryptosystem.
Principle to the full homomorphic encoding
Craig Gentry develop homomorphy encoding program including 4 techniques. They are the cardinal coevals, encoding, decoding algorithm and extra Evaluation algorithm. Fully homomorphic encoding incorporates two cardinal homomorphy types. They are the multiply homomorphic encoding algorithm and additively homomorphic encoding algorithm.The generation and add-on with Homomorphic belongingss. Homomorphic encoding algorithm underpins merely add-on homomorphy and generation homomorphy before 2009. Fully homomorphic encoding is to detect an encoding algorithm, which can be any figure of add-on algorithm and generation algorithm in the encoded information. For merely, this paper utilizes a symmetrical wholly encryption homomorphic algorithm proposed by Craig Gentry [ 4 ]
Encoding algorithms
The encoding parametric quantities p, Q and R, where P is a positive uneven figure, Q is a big positive whole number, P and Q determined in the cardinal coevals stage, P is an encoding key, and R is a random figure encrypted when selected.
For the text m, computation
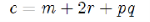
Then you can acquire the cypher text.
Decoding algorithms
To plaintext
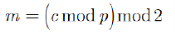
Because the p?q is much less than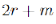 , so
, so
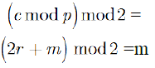
Homomorphism verification
The homomorphy linear belongings confirmations
Suppose there are two groups of the plaintext M1 and M2. To scramble them turn into the cypher text.
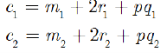
To plaintext
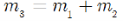
Due to
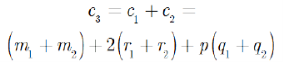 Equally long as the
Equally long as the
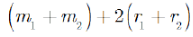 is much less than P, so
is much less than P, so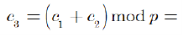
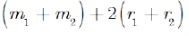
This algorithm fulfills the linear homomorphic conditions
The homomorphic multiplicative belongings confirmation
To plaintext
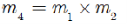
Due to
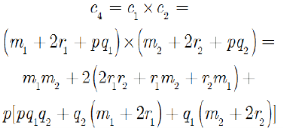 Equally long as the
Equally long as the
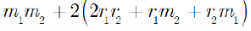 is much less than P, so
is much less than P, so
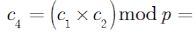
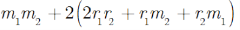
This algorithm fulfills the multiplicative homomorphic conditions
Application scene and security architecture
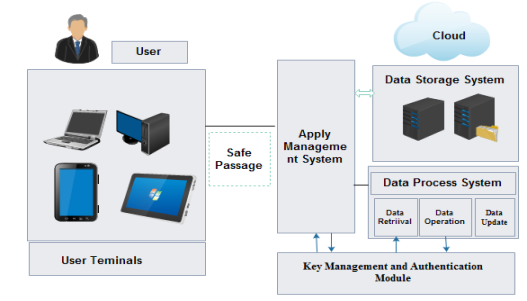
Privacy protection
User is hive awaying their informations in cloud, by agencies of security it is stored in encrypted signifier and while conveying the informations cloud service supplier and user ensures that plaintext information can non be found to others. That implies both will guarantee the safe storage and transmittal of informations.
Datas processing
Fully homomorphic encoding constituent empowers clients or the sure 3rd party procedure cypher text informations squarely, instead than the original informations. Users can get figure of arithmetic consequences to decode to acquire good information. for illustration, in medical information system, electronic medical records are in the signifier of cypher text and are stored over the cloud waiter.
Retrieval of cypher text
Fully homomorphic encoding engineering based on retrieval of cypher text method, FHE non merely ensures the privateness and efficiency of retrieval but besides the retrieval informations can be added and multiply without altering the plaintext.
Decision
Security is the most widely recognized issue for Cloud Computing. While hive awaying, conveying and recovering the information from cloud server security substructure is needed. Encoding is the common engineering to guarantee the informations security of cloud calculating. To supply precaution to net and overcast services Gentry proposed Fully Homomorphic Encryption ( FHE ) strategy from his old encoding theoretical account i.e. , slightly homomorphic encoding strategy.
Taking into history the cloud security issues this paper presented the thought of to the full homomorphic encoding strategy and proposed a security architecture which ensures the security of transmission and storage of informations over the cloud waiter
References
- new wave Dijk, M. , Gentry, C. , Halevi, S. , Vaikuntanathan, V. : Fully homomorphic encoding over the whole numbers. In: Gilbert, H. ( ed. ) EUROCRYPT. LNCS, vol. 6110, pp. 24–43, 2010.
- hypertext transfer protocol: //epubs.siam.org/doi/abs/10.1137/120868669
- Rivest R, Adleman L, Dertouzos M. On informations Bankss and privateness homomorphies Academic Press, pp.169—180, 1978.
- Gentry, C. , Halevi, S. : Implementing Gentry’s fully-homomorphic encoding strategy. Preliminary version ( August 5, 2010 ) , hypertext transfer protocol: //researcher.ibm.
- Wikipedia. Cloud calculating [ EB/OL ] . hypertext transfer protocol: //en.wikipedia.org/wiki/Cloud_Computing, 2012-12-05.
- Feng Zhao, Chao Li, Chun Feng Liu, “ A cloud calculating security solution based on to the full homomorphic encryption” IEEE 16ThursdayInternational Conference, pp.485-488, Feb 2014.
- Jian Li, Danjie Song, Sicong Chen, Xiaofeng Lu, “A simple to the full homomorphic encoding strategy available in cloud computing” . IEEE 2neodymiumInternational Conference ( Vol-01 ) , pp. 214-217, Nov 2012.
Cite this Page
Cloud security architecture based on fully homomorphic encryption. (2018, Sep 07). Retrieved from https://phdessay.com/cloud-security-architecture-based-on-fully-homomorphic-encryption/
Run a free check or have your essay done for you


