Software and Hardware System Requirements for a Project
Chapter 5
Requirement Analysis
The chapter describes security model demand and which is categorized on the footing of user interaction and specification of package and hardware demand. Besides its overview regulations assign to the assorted user.
Order custom essay Software and Hardware System Requirements for a Project with free plagiarism report
 450+ experts on 30 subjects
450+ experts on 30 subjects
 Starting from 3 hours delivery
Starting from 3 hours delivery
5.1 Software Requirement
| Name | Details |
| Operating System | Windows XP and Upper |
| Database Server | MySql, XML |
| Front End | Netbeans 7.2, JSP, Java SDK 6.0 |
| Application Server | Tomcat 6.0 |
| Browser | IE 5.0 and Upper or Mozilla, Google Chrome |
Table No 4.1 Software Requirement
5.2Hardware Requirement
| Name | Details |
| Processor | Pentium IV and supra |
| Random-access memory | 256MB and above |
| Hard Drive | 40 GB |
| Network | Local area network |
Table No 4.2 Software Requirement
5.3High Level Process Diagrams
A high degree description of the demands of the undertaking is to manage specifically defined maps utilizing a common platform, whilst other maps for content, enrollment, individuality direction and increasing security to single applications will be outside the range of the undertaking and this range is detailed in the diagram below:
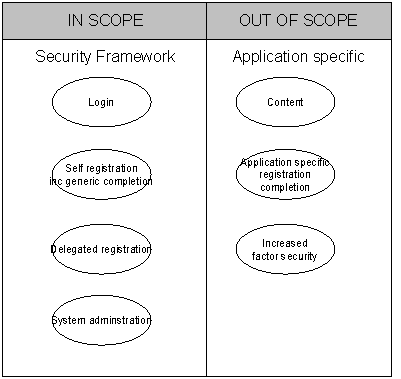
Figure 5.1: Scope of the Undertaking
This stage of the undertaking will cover individual factor hallmark and will merely capture username and watchword to authenticate a website user.
The demands are split into four subdivisions:
- Generic demands
- Self disposal functionality
- Delegated disposal functionality
- Help Desk disposal.
The generic demands will embrace certain facets that are generic across ego disposal and delegated disposal functionality. The undertaking will present the following generic demands for self disposal and delegated disposal:
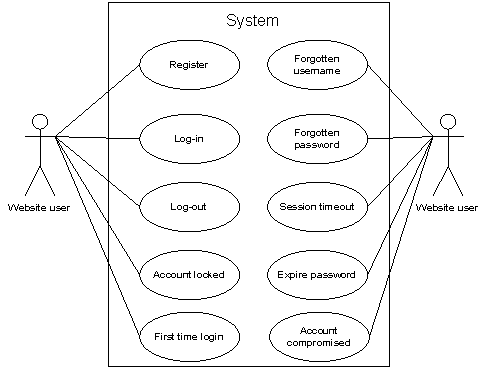
Figure 5.2: Generic demands for self disposal and delegated disposal
The undertaking will present the following self disposal functionality:
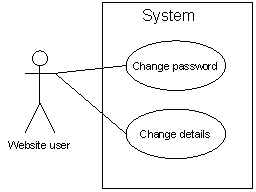
Figure 5.3: Self disposal functionality
The undertaking will besides present the followers delegated disposal functionality:

Figure 5.4: Delegated disposal functionality
There will besides be the undermentioned Help Desk disposal functionality that will be delivered by the undertaking:
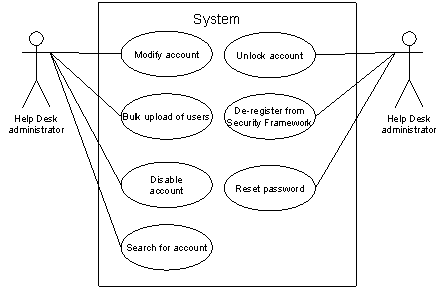
Figure 5.5: Aid Desk disposal functionality
5.4 User groups
| User group | Description |
| External web site user | An external web site visitant to any web site or application |
| Administrator | An internal decision-maker who will hold the capableness to supply entree direction to application-specific external web site users |
| Help Desk Administrator | An internal decision-maker who will hold the capableness to back up the security model and users of the model |
Table No 5.3: User Groups
5.5.1 Generic demands
Table No.5.4: Generic demands
| GEN-0011-Rule-2 | For Self disposal and decision-maker for delegated disposal enrollment signifiers, the information Fields must be blank on the first burden of the signifier. |
| GEN-0011-Rule-3 | The system will non auto-generate usernames for decision-makers for delegated disposal. The usernames will be entered manually. |
| GEN-0011-Rule-4 | When the web site user receives the invitation electronic mail and clicks the URL to lade the enrollment signifier, the username on the signifier will be pre-populated and not-editable. |
| GEN-0011-Rule-5 | Auto-complete must be set to murder. |
| GEN-0011-Rule-6 | Password and replies to security inquiries must be obscured. |
| GEN-0011-Rule-7 | The username can non be an email reference. |
| GEN-0011-Rule-8 | The website user must put up 4 security inquiries, of which 2 will be indiscriminately shown during future hallmark procedures. |
| GEN-0011-Rule-9 | Security replies must non: Be clean; Repeat replies across the inquiries; Be an individual figure or character replies. |
| GEN-0011-Rule-10 | The replies to the security inquiries will be a minimal 3 alphameric characters, with a maximal 20 alphameric characters and must non incorporate the undermentioned particular. |
| GEN-0011-Rule-11 | Website users will merely be registered for applications/websites within a pre-defined group, i.e. for either BHW applications or international applications |
| GEN-0011-Rule-12 | The format of the username will be a minimal 6 alphameric characters, with an upper limit of 20 alphameric characters and must non incorporate the undermentioned particular |
| GEN-0011-Rule-13 | The format of the watchword will be a minimal 8 alphameric characters, with an upper limit of 20 alphameric characters and must be instance sensitive. |
5.5.2 Self disposal demands
| Rate No. | Provide registered and logged in website users with self disposal capableness to alter their generic security inside information |
| SA-0020-Rule-1 | A website user will non be able to amend the username. |
| SA-0021 | The system must direct an electronic mail to the registered web site user when an amendment has been made to their inside information |
| SA-0021-Rule-1 | The electronic mail must province which inside information has been amended, but on what the inside information has been changed from or to. |
| SA-0021-Rule-2 | If the web site user has amended their electronic mail reference, the system must direct an electronic mail to the old and new electronic mail references advising of the amendment. |
Table No. 5.5: Self disposal demands
5.5.3Delegated disposal demands
| Rate No. | Description |
| DA-0010 | Provide decision-makers with delegated disposal capableness to make history for external web site users |
| DA-0010-Rule-1 | decision-makers will merely be able to register Website users for applications/websites within a pre-defined group, i.e. for either BHW applications or international applications. |
| DA-0010-Rule-1 | decision-makers will non be able to utilize the same username across pre-defined groups as the username must be alone. |
| DA-0011 | Provide decision-makers with the ability to advise website users of their enrollment inside information via an invitation electronic mail |
Table No 5.6: Delegated disposal demands
Software and Hardware System Requirements for a Project. (2018, Sep 17). Retrieved from https://phdessay.com/software-and-hardware-system-requirements-for-a-project/Cite this Page
Run a free check or have your essay done for you


